Security should be the number one priority for any company with sensitive data. Securing data goes well beyond password-protection. There are two common types of security that most companies in industry use - even if they don’t know it: Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC). Let’s walk through RBAC and ABAC, and look at how these security policies are used to deter unwanted data leaks and unauthorized access.
What is Role-Based Access Control?
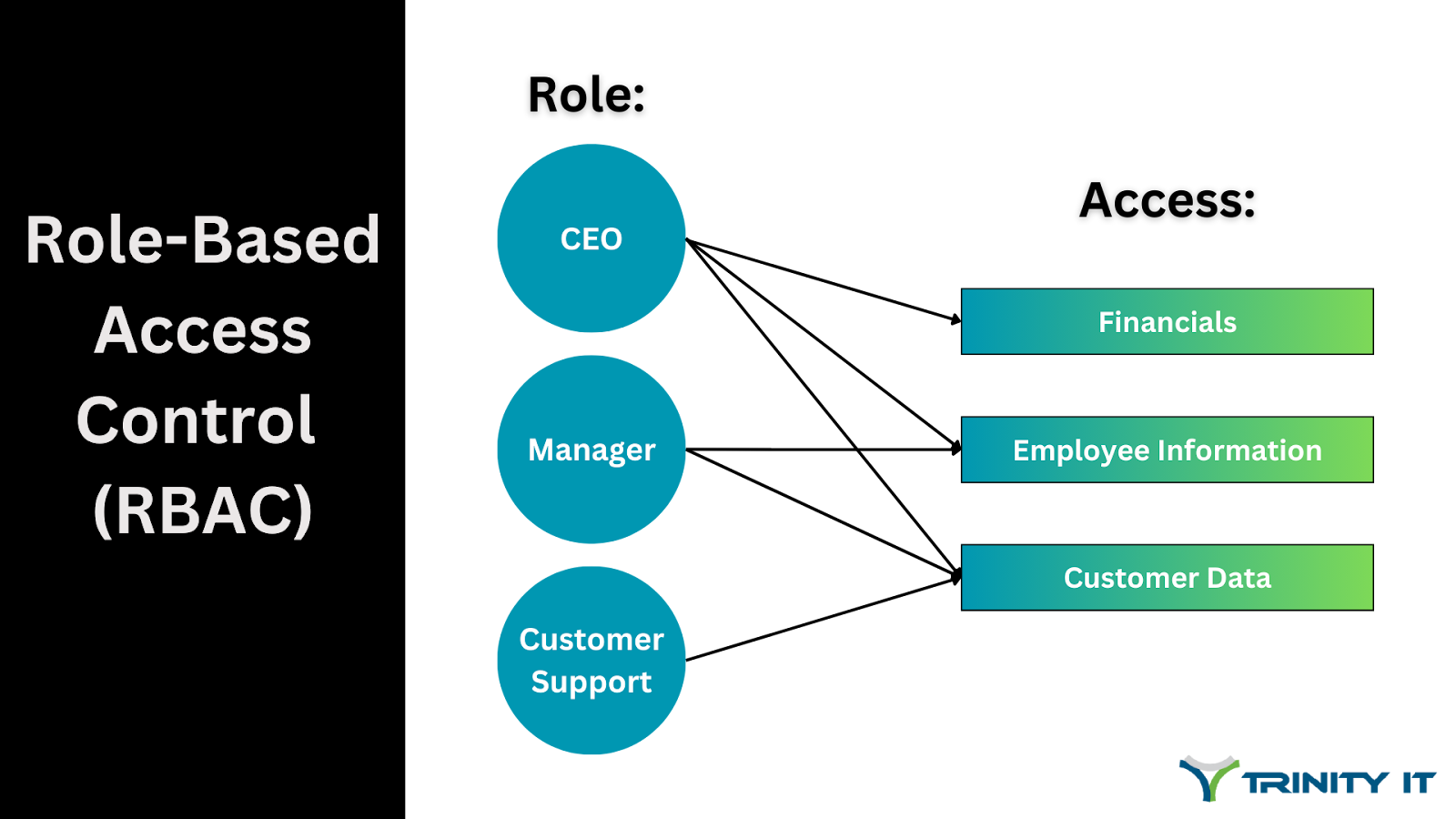
RBAC refers to the level of access or “permission” one is granted within a system, and it is dependent on that person’s role (whether in the organization or in each individual system). RBAC is used for security and efficiency by managing who can and cannot access specific systems and information. Not only is this optimal from a security perspective - especially in government industries - by limiting the people that know and perform certain functions, but it’s also beneficial in preventing crosswires and confusion in the division of responsibility. If access is denied from the first step (using a system), there will be no room for error in having the wrong person complete a task.
RBAC is a great way to maintain a collaborative environment with proper security measures in place. This helps protect important data from being altered or deleted by people in a non-authoritative role. It also helps prevent data breaches with the restricted access among lower-level roles that may not have adequate competence in security best practices. For example, a CEO would have access to everything within a company, while a department manager may have access to everything only within their department. An entry-level worker would only have access to data that directly pertains to their job responsibilities.
What is Attribute-Based Access Control?
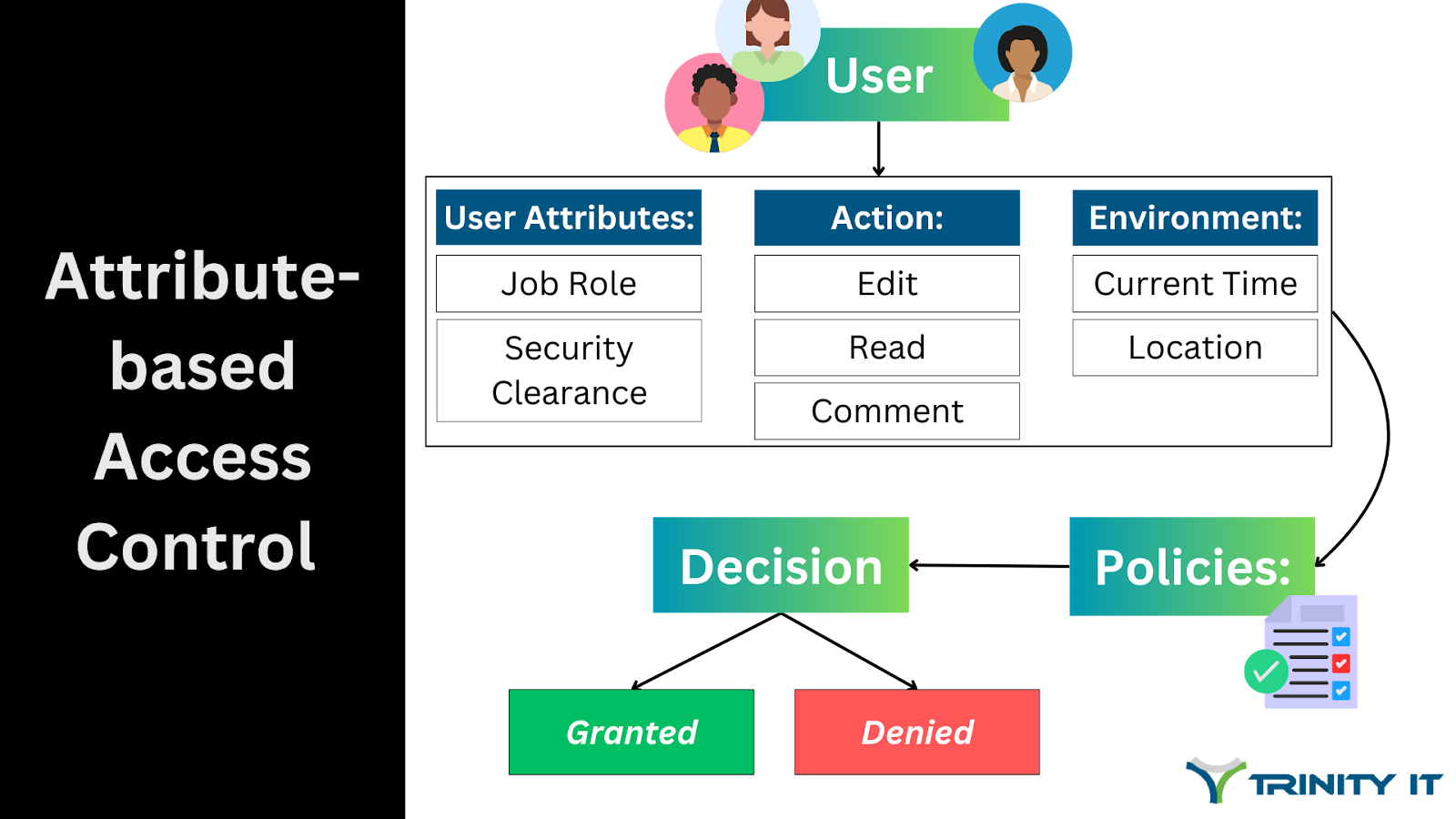
ABAC is more flexible than RBAC as it considers multiple factors, or attributes, to grant someone access to a system or information. Often with ABAC, an individual’s role in the organization is still important, but other attributes that may be required include time of day, location, security clearance, job title, etc. Each organization chooses which attributes are important for access, which is what makes ABAC more flexible. For example, in government industries, ABAC might include security clearance. Information is categorized by “need to know” and has various levels of security clearances. Some information may not require a clearance at all, while others require a specific clearance. For industries that are not involved with the government, these clearances are not relevant and not used.
ABAC is more flexible, but that does not make it any less secure than RBAC. Their effectiveness relies on the complexity of each organization’s needs. A smaller organization may need the rigid structure of RBAC to efficiently operate. Other larger, more complex, organizations need the multifaceted fluidity of ABAC. Many companies apply both methods of security depending on the systems they use.
How Trinity IT uses RBAC/ABAC
Trinity IT is one of many companies that uses both RBAC and ABAC security policies to appropriately handle the complex levels of security we need. As a whole, our company uses ABAC to implement security policies applied to company laptops and mobile devices. Our team uses internal ABAC policies to comply with security policies required for federal contractor companies.
The other work performed within the company, like our collaboration tools and back office work, applies RBAC security measures. Team members are assigned roles within systems like our customer relationship management system that determines the level of authority that they have. These roles will grant access to a hierarchy of functions within the system, from baseline viewer to superintendent access. We have several roles defined, where each role has different permissions for data access. We specify the permissions for the roles and then link the required roles to each end user. This allows us to manage permissions through roles instead of applying them to each end user account.
RBAC and ABAC are both excellent methods to maintain security and efficiency within an organization. The potential application of each is dependent on the data security requirements, so it’s important to understand your organization’s needs before determining which security methods are best.
,
